SAML Auth Managed Offering
Okta Set-up
You'll need the SAML-IDENTIFIER from us, unique to your org. We'll provide this once we start setting SAML up for you. You'll be entering it in the instructions below.
Create a new Okta App Integration:
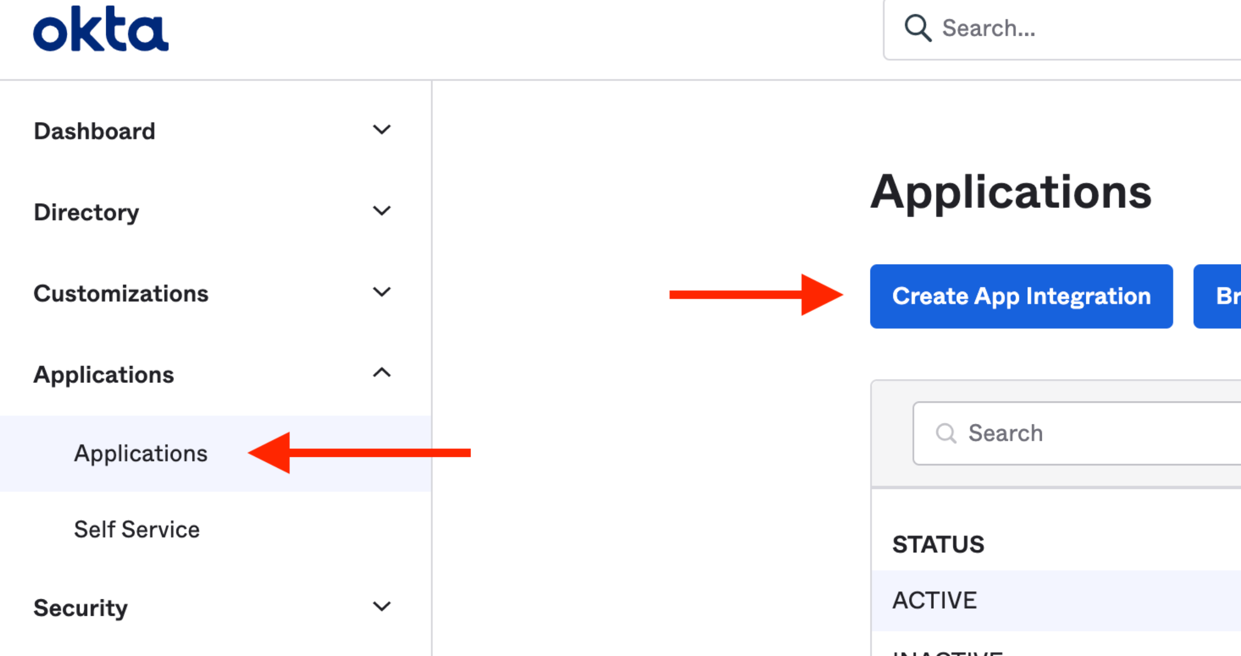
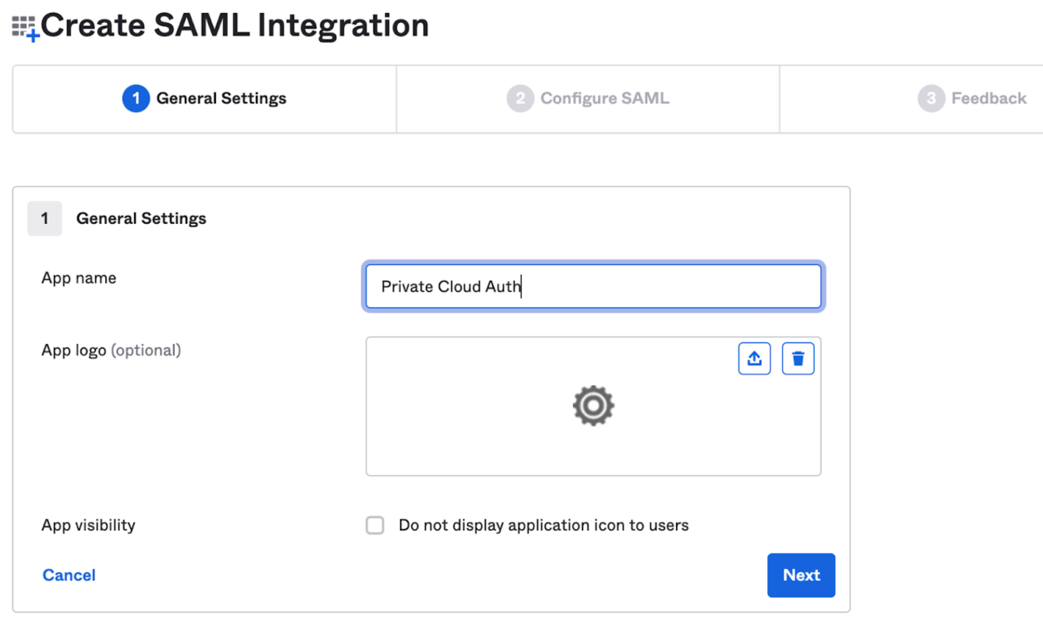
Give it a name:
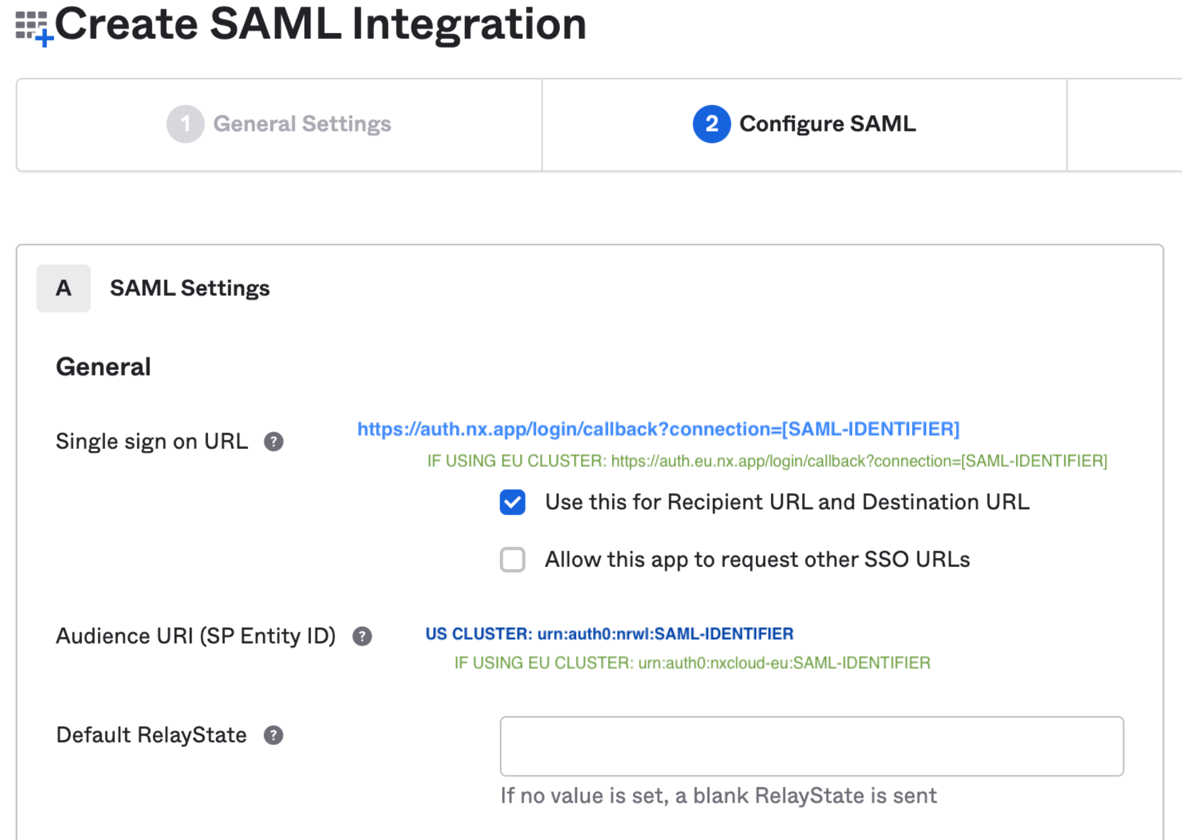
On the Next page, configure it as below:
- The Single Sign On URL needs to be:
- If using the main-US cluster:
https://auth.nx.app/login/callback?connection=SAML-IDENTIFIER - If using the EU cluster:
https://auth.eu.nx.app/login/callback?connection=SAML-IDENTIFIER
- If using the main-US cluster:
- The Audience should be
urn:auth0:nrwl:SAML-IDENTIFIER- If using the main-US cluster:
urn:auth0:nrwl:SAML-IDENTIFIER - If using the EU cluster:
urn:auth0:nxcloud-eu:SAML-IDENTIFIER
- If using the main-US cluster:
- The Single Sign On URL needs to be:
Scroll down to attribute statements and configure them as per below:
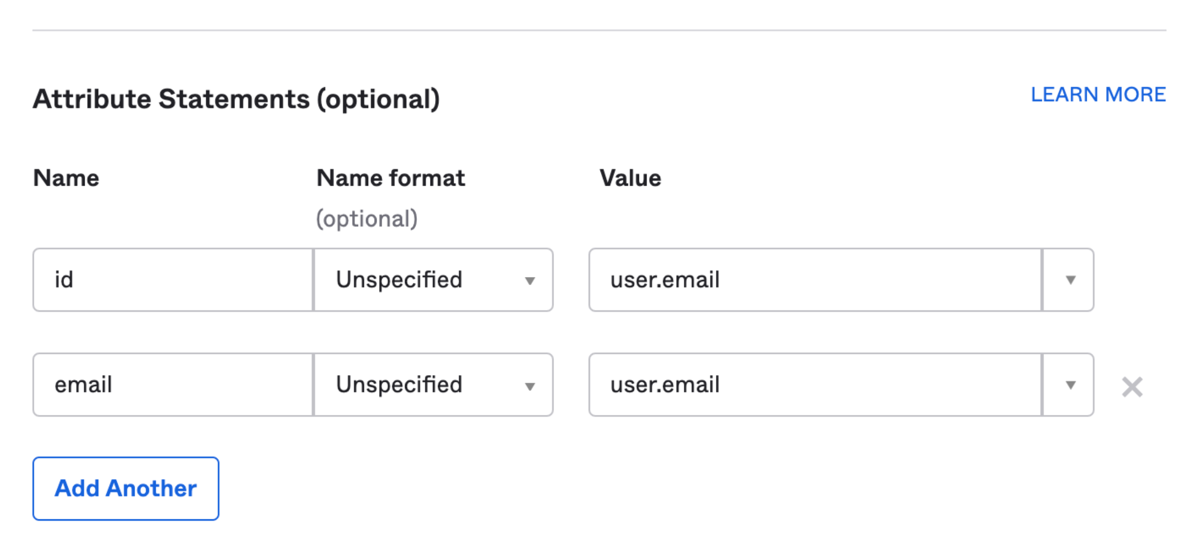
Click “Next”, and select the first option on the next screen.
Go to the assignments tab and assign the users that can login to the NxCloud WebApp:
- Note: This just gives them permission to use the NxCloud web app with their own workspace. Users will still need to be invited manually through the web app to your main workspace.
Then in the Sign-On tab scroll down:
Scroll down and from the list of certificates, download the one with the “Active” status:
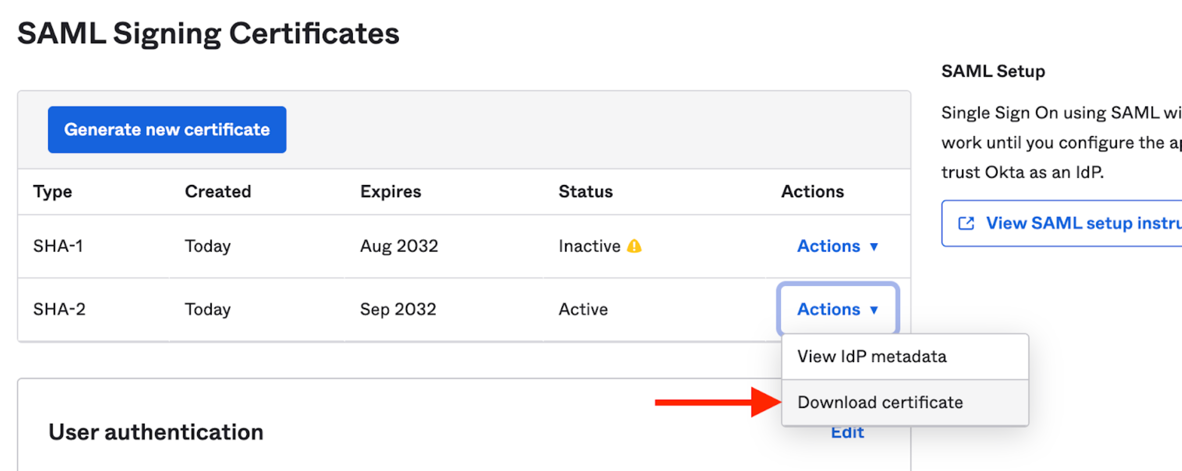
Then view the ldP metadata:
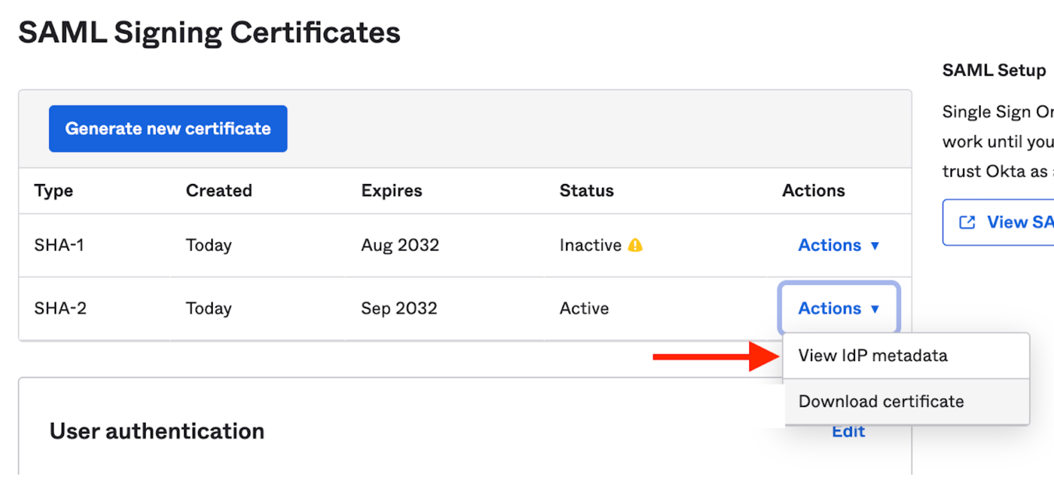
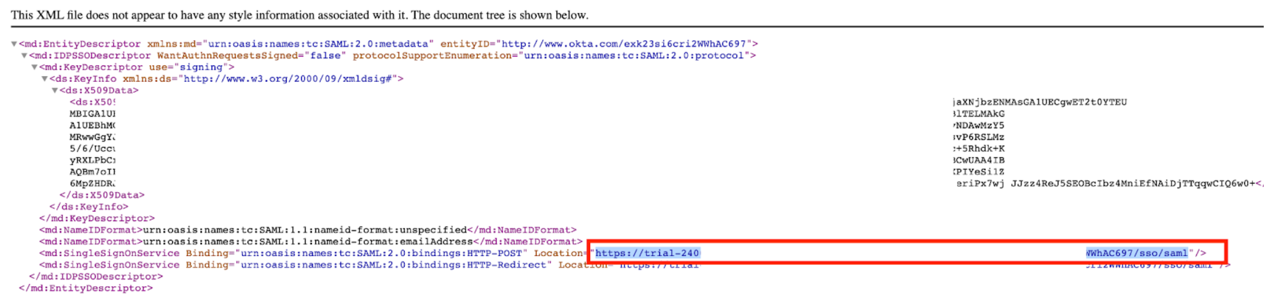
Then find the row similar to the below, and copy the highlighted URL (see screenshot as well):
1<md:SingleSignOnService 2 Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" 3 Location="https://trial-xxxxx.okta.com/app/trial-xxxxx_nxcloudtest_1/xxxxxxxxx/sso/saml" 4/> 5
Send us via email:
- your public certificate downloaded in step 8
- your URL from step 10